
Aug 17, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Data breaches have become so common that they are no longer news. Gartner predicts, “as more companies look to benefit from data, there will be an inevitable increase in data use and sharing missteps.” However, organizations that have a culture of ethics for data use will be better prepared to avoid such mistakes, and to handle them well if they do occur. Read on to learn how your company can have not just a data protection plan, but a culture that revolves around protecting the personal data of your customers. Protecting Your Business and Your Customer’s Data In spite of the occurrence of data breaches, your company can be protected. If you haven’t already done so, you might draw up a data-protection plan that will address what to do in case of a breach. Ideally your organization will already have technology in place to prevent data breaches–tools such as updated antivirus and anti-malware definitions and network monitoring, for instance. Hopefully, there is also a culture of ethics around use of customer information, including transparency with customers about what is done to protect their personal data. Countries and entire regions, such as Australia and Europe, have put legislation into effect to protect customers. Europe’s GDPR mandates a notification within 72 hours of a data breach. Australia’s Consumer Data Right gives its citizens the right to delete information that is no longer needed, as well as stopping data collection at any time While the U.S. has no nationwide law, individual states have their own regulations. For example, California gives their residents certain rights under the California Consumer Privacy...

Aug 10, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
While many businesses have already adopted cloud computing to a certain extent, others are still new to the technology. Whether your business is using cloud computing already, or is considering a move, it’s never too soon to develop a strong strategy. Read on to learn more about developing a strategy to guide your business in considering cloud computing. Strategy, Then Implementation A key feature of a cloud strategy is that it addresses why a company might move some or all of its operations to the cloud. According to a report by Gartner, “a cloud strategy explores and defines the role that cloud computing should play in an organization.” Formulating a strategy is a task of the entire organization, not simply the IT department. Departments such as human resources, legal and finance can provide valuable input, since they will use the computing resources that the cloud can provide. A company that has already moved some of its data and applications to the cloud can also develop a strategy moving forward. It’s easy to assume that if a business has moved to the cloud, it’s too late to develop a strategy. Quite the contrary, a strategy can help refine a company’s motivation for adopting cloud technology, based on lessons already learned. Strategists can examine how the cloud has benefited the business so far, meeting its needs (conforming to data regulations, for instance). Along with accomplishments, it gives a business the opportunity to correct any mistakes going forward. Once a strategy has been formulated, then implementation (including choosing a provider and a cloud environment) can begin. Contingency Plans as Part of Your...

Jul 20, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Your organization’s computer network is the backbone of your IT operations, supporting data and applications such as Voice-Over IP (VoIP), call center and more. Monitoring this network can help save time and money. Read on to learn more about the benefits of network monitoring, and what to consider before adopting a solution. Benefits of Network Monitoring Network monitoring is a proactive way to detect and mitigate threats to your network’s security. One key function of network monitoring is identifying and solving small problems before they become larger issues. Network monitoring can identify possible intrusions from virus and malware, stopping data breaches before they occur and saving your business money and reputation. Network monitoring also helps identify any bottlenecks and reroutes traffic to keep data flowing, allowing your system to adapt in real time and data-intensive applications like VoIP and call centers to operate at their best. Why Monitor Your Network? Before adopting a network monitoring solution, consider the most critical needs of your network. One factor is your IT budget; how much should you allocate to avoid unnecessary downtime and performance issues? Loss of productivity, inability to service or communicate with customers and other business interruption can add up. Another factor to consider is how you will respond to remediate any notifications and alerts. With businesses partially closed because of COVID-19, remote network monitoring might be the best option. Remote monitoring constantly looks for potential bottlenecks and intrusions, removing the need for an on-site visit. Remote monitoring and management provides additional operating system patches and ensures anti-virus and anti-malware definitions are current to block possible data breaches. Again, this...

Jul 13, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Cloud computing is now a common way for small to medium-size businesses to provision computing resources for flexible, cost-effective results. Read on to learn about how one cloud model–Infrastructure as a Service or IaaS–can help your business manage spend and maximize results. IaaS Provides Flexibility According to Gartner, Infrastructure as a Service (IaaS) is a standardized, highly automated offering, wherein computing resources, complemented by storage and networking capabilities are owned by a service provider and offered to the customer on demand. With the infrastructure owned and managed by the cloud service provider, the business using the resources no longer needs to maintain infrastructure on-premises. The business can let the provider do the work of maintenance and updating, which converts a capital expense to an operating expense paid on a monthly or annual basis. In an IaaS model, a company can purchase extra resources for experimental technical initiatives, then scale back when needed. On-site infrastructure is available, to which new applications can be added. What to Consider Before Adopting IaaS Infrastructure as a Service, with its many benefits, still needs to be evaluated according to business needs. Some companies such as health care organizations are subject to compliance with HIPAA and HITrust, and will need a private cloud environment. Encryption of health-care data is vital, when it is in motion (as in the case of a telehealth appointment) or at rest. IaaS offers the most control for health-care organizations, including the ability for IT admins to modify how data is handled and stored. While some organizations might need to spend more for this level of security, maintaining security and compliance...

Jun 17, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
It is never too soon to consider what your business will do in the event of a disaster–a cyber attack, a natural disaster, or an epidemic. In the Covid-19 pandemic and subsequent quarantine, many businesses have still managed to continue operating with employees working from home. These times have been a test of any business continuity plan and have also proved the need to have a plan in place. Read on to learn more about developing and refining a plan for your business in these challenging times. Business Continuity Goes Beyond Data A key element in any business continuity plan is handling data—storage, transmission and protection. Data is the lifeblood of your business, and must be readily available and kept safe from loss and compromise. Questions to consider include whether data will be stored on site, in the cloud, or both; which mission – critical data needs to be readily available; and how that data will be backed up. Also, how do you protect proprietary information with employees working remotely, under varying conditions? With employees working remotely, the risks are higher. If there is a cyber attack, who will handle it, and how? Another consideration is the human element — caring for employees and customers during the on-going quarantine. Caring for Employees and Customers This pandemic–or any disaster–offers an opportunity for companies to become trusted leaders for employees and customers alike. According to CompTIA, one way to guide employees through a disaster situation is to communicate proactively with them. You can share both good and challenging news with them, in order to reassure them. Topics to talk about with...
Jun 12, 2020 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
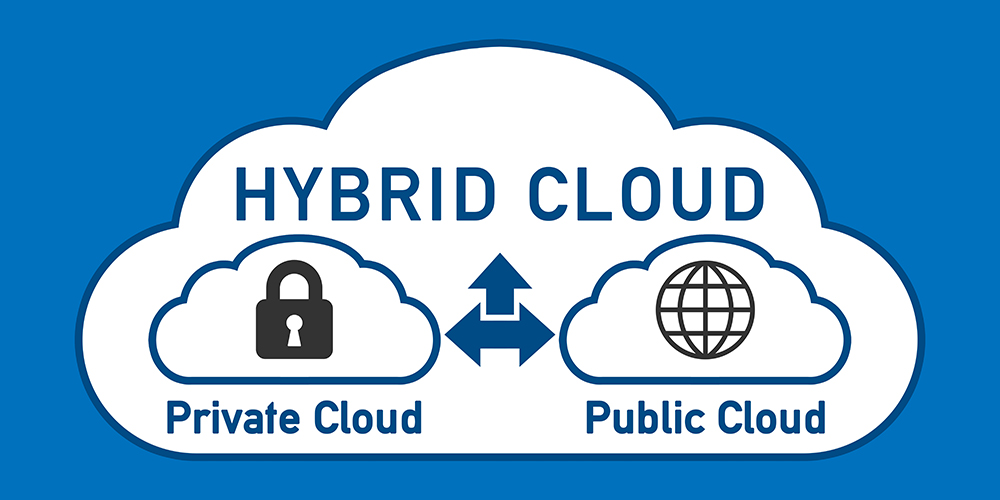
Cloud computing, once an emerging technology, is now common, and is proving valuable in this time of remote work resulting from the COVID-19 quarantine. To access data and applications, all that is needed is a computer and an Internet connection. Each type of cloud environment–public, private, and hybrid–comes with its own benefits and considerations. Read on to learn more about what each offers, and to consider which is best for your business. Benefits and Considerations of Public and Private Cloud Environments While all cloud environments have benefits, your business’ needs will impact which one you choose. Public cloud, often used by businesses, schools, and government organizations, is the least expensive, and is easily accessible. All that’s needed is a computer with access to the Internet. Public cloud, like other cloud environments, is flexible and easily scalable, depending on how much demand your business receives. A consideration is sharing computing resources with other entities, and how much bandwidth is available. Another question to ask your IT professional is security of data during migration to the public cloud, and once it resides there. Private cloud environments, in contrast, can help a company keep its data and applications secure, since the public cloud environment is used exclusively by one organization. For organizations needing to follow data-protection regulations, they might ask about private cloud. Private cloud has the same flexibility as public, with added security. Considering a Hybrid Cloud Environment A hybrid cloud environment is a combination of on-premise, third-party, public cloud and private cloud, with some infrastructure owned and used by a business, and some owned by a cloud service provider. A...







