
Dec 6, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Last year at this time, it was predicted that technologies like 5G and Internet of Things would be developing trends. This is still true. According to a survey by CompTIA, the global tech industry is set to grow at a rate of 3.7%, reaching $5.2 trillion. The United States technology market accounts for nearly a third of that, with an expenditure of $1.7 trillion expected in 2020. Read on to learn more about business’ approach to the adoption of these new technologies. New Technologies Making Inroads in 2020 While technologies of infrastructure and software development (Internet of Things and Artificial Intelligence, respectively) will continue to gain ground, for many businesses they are secondary to the infrastructure and software development that already exist. Some other emerging technologies mentioned by CompTIA include software development (Software as a Service, for instance) and big data analytics. These technologies that are coming to the fore may drive revenue growth, once they are integrated with already-present technology to create innovative solutions. The Four Pillars of Information Technology According to an IDC survey, companies plan to orient their technology spending to four “pillars” of information technology: software development, cybersecurity, data, and infrastructure. Of the companies surveyed, 57% plan to focus on software development. With the infrastructure already in place, along with the users and connectivity being available, U.S. companies can focus on developing the software and services supported by this foundation. Cybersecurity follows close behind, with 51% of surveyed companies focusing on expanding their defenses against cyberattack and establishing internal processes and policies to keep their operations secure. A portion of companies (47%) will choose to...

Nov 13, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
With so many organizations generating data in the course of daily business, it’s more important than ever to protect it from loss or compromise. Data breaches are frequently in the news, and aside from the negative publicity, result in fines and loss of revenue for companies. Maintaining network compliance is critical for all businesses. Read on to learn how to protect your company from this costly scenario. Network Compliance is Helpful to a Company’s Security Security has to do with a company’s own technology assets, whereas compliance can be defined as a company adhering to policies and procedures. For most companies, network compliance may be scheduled backups, operating system patching and anti-virus updates. For companies with regulatory requirements of a third party, such as a government or industry compliance involves more than simply protecting an individual company’s assets, though doing this can be helpful in progressing toward compliance. Industries can have strict regulations; HIPAA, for example, protects the privacy of patients’ health care data. Another category, which serves as a standard, is Payment Card Industry Data Security Standard (PCI-DSS); it protects the payment card data of people shopping online. These industry regulations carry strict requirements for the protection of personal data, and company networks must comply or face penalties. With threats abounding, such as malware and viruses, or simply a hole in the network, a network’s protection is crucial. Ways to Keep Your Network Secure and in Compliance One way to get a baseline for evaluating the security and compliance of your network is to conduct a network audit, taking an inventory of the network itself along with all...
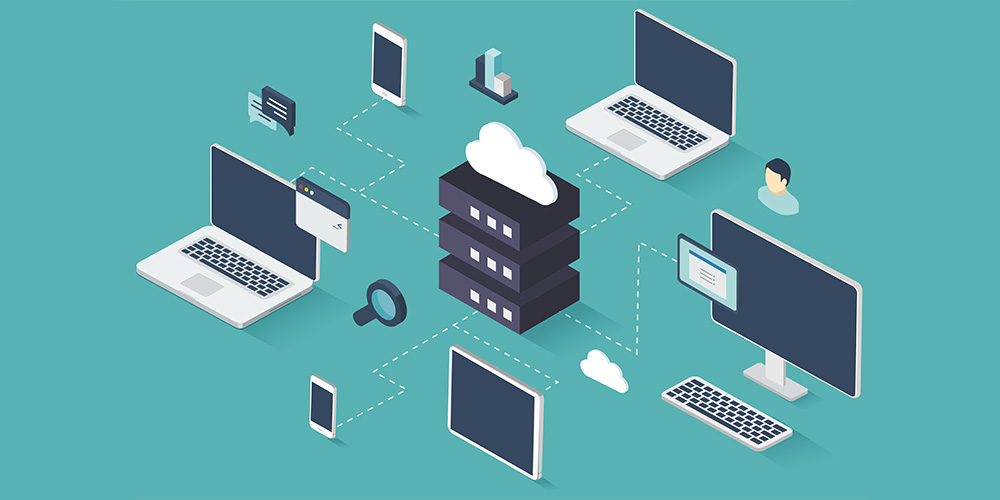
Nov 7, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
With companies seeking the best return on investment for their technology expenditure, Cloud migration, or, in some cases, migrating to a different Cloud environment or changing to a new Cloud provider, can be a good choice. Read on to learn more about the benefits of using the cloud as well as what to consider before migrating. Benefits of Cloud Computing Cloud computing, which has become more common over the last decade or so, is a model whereby businesses can store and access data and other computing resources via the Internet. Benefits include predictable costs and flexibility. With cloud computing, the cloud service provider furnishes and maintains the infrastructure, converting burdensome capital expense to a more flexible operating expense. Models of cloud computing include Software as a Service (SaaS) and Infrastructure as a Service (IaaS), among others. Both of these cloud segments offer the advantage of off-site infrastructure; in the case of SaaS, the software is provided. Cloud computing can be billed on a monthly or annual subscription basis, and the cost of initial migration may be spread out over time. Along with these economic benefits, migrating to the cloud necessitates a company to evaluate its needs and goals. Considering a Cloud Migration Before a Cloud migration, businesses need to consider their reasons for doing so and which Cloud environment is best. Some businesses need to keep their customers’ or clients’ data compliant with industry regulations such as HIPAA, in which case a private cloud environment may be preferred. Others may need the flexibility of a public Cloud solution. Still others may be turning to the Cloud with business continuity...

Oct 15, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Imagine if no matter how well protected your computer systems are, there was yet another level of protection? One which involves specific factors particular to the user, which they can use in addition to a strong password? With multi-factor authentication (MFA), you have yet another defense against bad actors seeking to infiltrate your network. Read on to learn more about this relatively new technology. MFA: An Extra Layer of Protection Passwords used to be enough. However, with bad actors looking for—and finding—ways to get into your network, multi-factor authentication (MFA) is a technology that is gaining ground. The most common type of this validation is two-factor authentication, in which a second method (additional factor of verification) is used to validate your account. For example, using a password (one factor) and text message with a code (second factor). The use of two different factors enhances security the way a single factor can’t. These details are not ones a bad actor will know, so even if they access the system using your password, they cannot go any further. An introductory article from the National Institute of Standards and Technology (NIST) cites studies that indicate that users of MFA feel much more secure than with their passwords alone. Two-factor authentication is a subset of MFA and is adequate; using more than two factors provides even more protection. Applications to Core Systems and the Cloud With technology continuing to grow, threats follow closely behind. How do you keep “bad actors” from accessing your network, the backbone of your IT infrastructure? Some attacks, like ransomware-as-a-service, allow a cyber criminal to simply log in to...

Oct 3, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
October is National Cybersecurity Awareness month, a “collaborative effort between government and industry to raise awareness about the importance of cybersecurity, and to ensure all businesses have the resources to be safer and more secure online.” This year, according to the US Department of Homeland Security, the emphasis is on a proactive approach. Read on to learn more about various aspects of cybersecurity. Develop Awareness of Current Security Threats The more technology advances and expands, the more places an attack can occur. Cybercriminals are growing more clever and resourceful, and know how to insert malware, or a bot that can mimic human activity. There are also phishing schemes, wherein an attacker can send an email persuading an unwitting employee to share confidential data. Weak spots in a network are subject to exploitation as well. Many companies, according to CompTIA, think that security is “good enough,” and haven’t yet dedicated much of their budget to maintaining cybersecurity. However, your business doesn’t have to be one of them. There are steps you can take, starting with an assessment of your network’s security. Take an Inventory of Current Protections What is your current level of security? Take stock of your business’s protection, starting with the computer network. Are there any weak spots or vulnerabilities needing to be patched? Make sure that you have the most current operating system patches. Also ensure that your antivirus and anti-malware definitions are current, to block attackers from infiltrating your system. Map all devices connected to your network, including ones operated by staff working remotely to make sure that those points are safe. Do your employees know...

Sep 17, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
October is Cybersecurity Awareness month and knowing this can serve as a wake-up call to protect your company’s data, networks and systems from internal and external hazards. Read on to learn more about protecting your business. Cybersecurity—An Overview The overall goal of cybersecurity is protecting a business’ computer systems from attacks and intrusions, and your data safe from loss or compromise, preserving your business’ revenue and reputation. While natural disasters are always a factor–and preparing for them is a piece of the IT security puzzle—manmade hazards like viruses and malware are just as important to guard against Cyberattack. Not only that, phishing attempts—emails designed to get an unwitting recipient to supply private information—are a common threat. Fortunately, plenty of protections are available to help safeguard your business’ technological assets. Tools Can Help Keep Your Business Secure Many resources are there to help you protect your business and its network. Antivirus and anti-malware definitions, kept up to date, can guard your system against the newest threats. Operating system patches can protect weak spots in your system and should also be as current as possible. Network monitoring helps keep track of possible intrusions as well as bottlenecks that slow down data transmission. Last, but not least, your staff can be a key part of your strategy, if they are trained to recognize potential hazards. Enlist Your Employees in Fighting Cyber Attacks Your human resources have the potential to be a resource in maintaining the information security of your business. If well trained, in what to recognize and how to report it, your employees can protect you from an attack. Impress upon...







