
Aug 14, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
With technology ever changing and progressing, more is demanded from your network than ever before. Cloud computing, along with multiple applications and huge amounts of data, demand a strong and healthy network. Read on to learn more about how to monitor your network and maximize its flexibility, efficiency and security. Network Monitoring—The What and the Why Network monitoring is a proactive part of a managed services plan, alerting a business to hazards both within the network and attacks from outside. First, network monitoring can show where there are poorly functioning circuits leading to disconnections, or bottlenecks in the system. Network outages due to these causes, along with natural disasters and power outages, can cost a business in terms of loss of revenue, downtime, and loss of reputation from data leaks. Second, network monitoring can identify external threats such as denial of service attack and potential ransomware intrusion attempts. The Where and How of Network Monitoring If a hazard or intrusion is identified quickly, it can be dealt with quickly, keeping a problem from escalating. For example, it can find potential holes where data can be leaked or lost. Also, excessive bandwidth consumption can be identified, so that computing resources can be directed toward mission-critical applications. Unauthorized users can be detected, to protect the network from those who should access it. Software-defined Wide Area Networks (SD-WAN) is a system in which multiple carriers are used, affording the business additional flexibility; if one part of the network is down, another part can pick up the traffic, allowing for uninterrupted service. Remote network monitoring can save time and money by eliminating the...
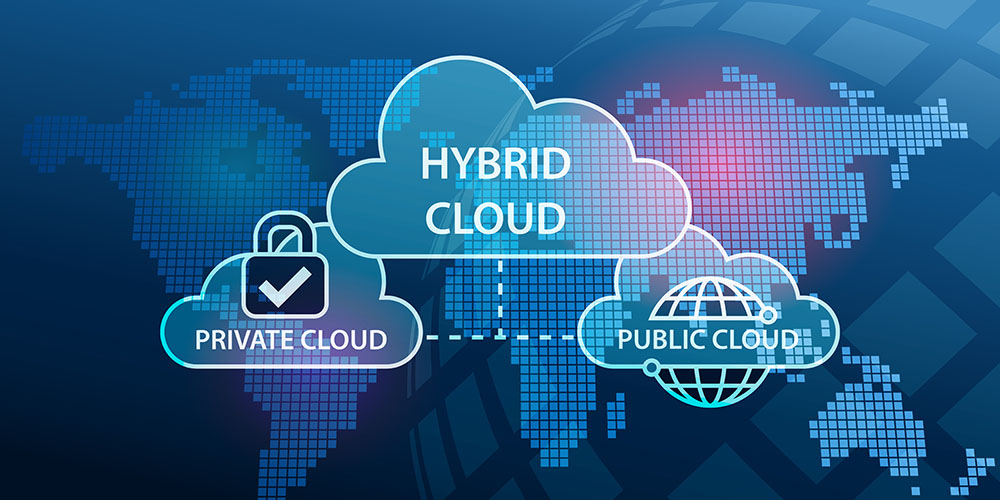
Aug 6, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Cloud computing, despite varying levels of adoption, has become a common way for a business to avail itself of computing resources without having to maintain expensive infrastructure. Companies can use varying levels of resources, scaling up and down as demand and usage changes. How does a company know which cloud environment is the right one? Read on to learn more about how to make this determination. What is Hybrid Cloud? Hybrid cloud is a combination of on premise, third party, private cloud, and public cloud. Some companies have moved all the infrastructure to the Cloud. This could include software as a service (e.g., Customer management system), or also infrastructure as a service for application hosting or Cloud backup. Other companies may choose to keep some services available on premise (at their location) for failover or easy access, while at the same time tapping in to public or private cloud services for off-site redundancy or access to new features that may not be available in legacy systems. Benefits of Hybrid Cloud Hybrid Cloud can offer flexibility and agility to a business, allowing you to get the best of both worlds. For example, having files locally can help you backup quickly in the case of ransomware attacks, without having to restore from the cloud. If you are in a disaster recovery scenario when you cannot access your physical location, private or public cloud can give your applications and data from most anywhere. Hybrid Cloud Considerations If you are combining on-premise, public cloud and private cloud in your business, it is important to have a solid network infrastructure to avoid bandwidth bottlenecks...

Jul 16, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
With the advance of technology, many benefits have come to businesses—commerce taking place twenty-four hours a day and the ability to have meetings with workers half a world away, among others—but cybercriminals have learned to exploit technology, using practices such as phishing (planting a fraudulent link in an email) to gain access to business’s data and networks. With social engineering, Phishing, and Spearfishing on the rise it is important for you to raise employee awareness about these threats. Read on to discover how to keep your business safe from this type of intrusion. What Phishing is and How to Prevent It Phishing is an increasingly popular way for attackers to access company data and plant malware in a network. A phishing attempt involves putting a fraudulent link in an email to get the recipient to click on the link and unwittingly import malware into their company’s network. Spear phishing, a related type of attack, focuses on an organization or individual. Employees can be trained to recognize an attempt by looking for clues. One is misspellings and grammatical errors in the message. Another tipoff is a strange or suspicious sender’s address; if it looks strange or suspicious, don’t open the email. Yet another practice is to point the mouse arrow over a link to look at it without clicking. All are things an individual can do, and there are additional effective practices. Focus on the Fundamentals The best preventive measures are simple. According to a CompTIA article, getting the basics right is one of the soundest investments a business can make. Prevention, as always, is far less costly than repair....

Jul 12, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
In the last week, two earthquakes have shaken southern California, alerting us to the need to have our businesses prepared for a disaster, whether natural or manmade. Not only can fires, floods and earthquakes cause business interruptions, but so can systems failures, human error, malware and ransomware attacks. It’s never too soon to evaluate what needs to be done to prepare your business for a disaster. And a disaster doesn’t have to be large-scale; a power outage of an hour or two can be enough to stall business operations. Read on to learn about the most important things to do before an emergency Make Data Protection a Key Part of Business Continuity Data is the lifeblood of many businesses, its loss or compromise affecting their ability to do business. Data is needed for transactions and communications, among other functions, and even a short period of downtime can have a potentially disastrous impact on revenue and reputation. When considering the data protection aspect of your business continuity plan, focus on your mission-critical data and applications. What do you need in order to stay in business during a disaster, or recover afterward? Perhaps it’s customer records, or an in-house research database. Be sure to get mission-critical data backed up first, so your business can continue operating. Make sure there is failover—when one network backbone falters, another picks up the slack. Different Methods Can Achieve the Same Goal While the ultimate goal is to remain in business without compromise of revenue or reputation, different methods exist to realize this goal. However, one common thread is the idea of storing data offsite, in...

Jun 18, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
Imagine being able to integrate business class phone systems, collaboration and virtual meetings and your contact call center all within a secure and reliable unified communications suite. This means you can work anywhere, get customer information instantly and route calls efficiently to communicate in real time all over the world. Increasingly, Unified Communications can integrate your office communications and help you help customers. Unified Communications Adoption Continues to Grow According to an article by Grand View Research, the market for Unified Communications is expected to grow to $167.1 billion by 2025, with a growth rate of 16.8% in upcoming years. Unified Communications, provides businesses a tightly integrated solution consisting of VoIP, along with applications such as video, web collaboration, and mobility. Three popular components of Unified Communications are Voice Over IP (VoIP) technology, web conferencing and call center technology. Voice Over IP helps businesses move from a private-branch exchange to a methodology that uses the Internet. Web conferencing allows companies to communicate with customers and employees in other parts of the world. Call center technology can speed communication through integration with CRM, to route the call to the best person to serve the customer. Benefits of Adopting Unified Communications Not only is UC an efficient way to integrate a business’ operations, it can help companies save money and increase revenue. Managers in the office can communicate with employees out in the field, and with voice mail that flows to email, employees in the office can get a quick answer to a question, or more information, with minimal wait time. The speed of processes can improve, helping a business gain...

Jun 12, 2019 | SMB Technology, SMB Technology, SMB Technology, SMB Technology, Technology News
In less than a year, support for Windows 7 will be ended, making operation systems patches and updates unavailable, according to a 2018 article. Since this will impact cybersecurity as well as compliance. Many companies are migrating to a new operating system. A key consideration is protecting your business from data loss and compromise, and in some cases complying with stringent regulations, such as, PCI-DDS and HIPAA. What are the risks inherent in migration, and how can a business navigate the migration? Read on to learn more about handling the coming change and keeping your data safe. Preparing for Windows 7 End of Service With the upcoming Windows 7 end of service, operating systems patches will no longer work on your devices, possibly leaving your network and data open to cyberattack. Not only that, if compliance to regulatory standards like HIPAA is required, a company may incur fines if data is lost or exposed to cyberattack. However, with a detailed plan and preparation, the transition can be made to the new operating system. First, as already mentioned, conduct an audit of all devices still using Windows 7. Determine which mission-critical data and systems need to remain accessible during the migration. Streamlining data and applications—removing old data and obsolete applications—can help alleviate the burden of moving unneeded assets. Once the audit has been conducted and a plan developed with the help of your IT advisor, testing can begin. Test Before Going Live Before going live with the new operating system, testing the plan is vital, to ensure that no data is lost or corrupted during migration. Testing should help identify...







